
. — MISP STIX — , legacy/deprecated: MAEC, IODEF, OpenIOC (Cybox), CAPEC, IODEF, VERIS . community- txt csv, , .
- : , TI. - , « » . , , TI . .
STIX
STIX, . , 1 2.1. : , , , , . , STIX:
STIX , . OASIS, cyber threat intelligence 50 , TI. — , , .
STIX TI , . , .
, STIX serialize-agnostic, JSON, GitHub. STIX , OASIS : STIX TAXII, HTTPS .
STIX , SDO (STIX Domain Objects), — SRO (STIX Relationship objects).
SDO STIX :
(Attack pattern) — (TTP), . , , , , .
(Campaign) — , .
(Course of action) — , , .
(Identity) — , .
(Indicator) — , (, IP-, , , ).
Intrusion set — , , , . Campaign , , , Intrusion set , Campaigns .
(Malware) — .
(Observed data) — .
(Report) — - , , TTP, . , , , , , , .
(Threat actor) — , , . , . Identity.
(Tool) — , . Malware , , , nmap RDP, VNC.
(Vulnerability) — / , , , , , .
, . .
№1
http://x4z9arb.cn/4712/ URL () x4z9arb backdoor. , — , (downloader), x4z9arb backdoor.
? : ( http://x4z9arb.cn/4712/) , , x4z9arb backdoor. , . , , Malpedia.
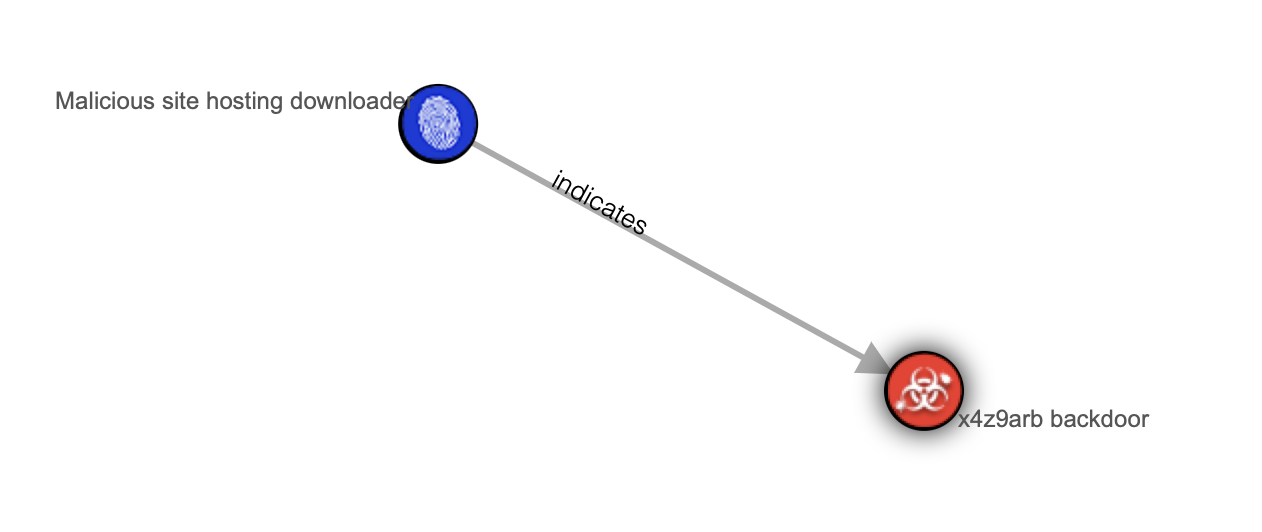
STIX 2.1
{
"type": "bundle",
"id": "bundle--56be2a3b-1534-4bef-8fe9-602926274089",
"objects": [
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--d81f86b9-975b-4c0b-875e-810c5ad45a4f",
"created": "2014-06-29T13:49:37.079Z",
"modified": "2014-06-29T13:49:37.079Z",
"name": "Malicious site hosting downloader",
"description": "This organized threat actor group operates to create profit from all types of crime.",
"indicator_types": [
"malicious-activity"
],
"pattern": "[url:value = 'http://x4z9arb.cn/4712/']",
"pattern_type": "stix",
"valid_from": "2014-06-29T13:49:37.079Z"
},
{
"type": "malware",
"spec_version": "2.1",
"id": "malware--162d917e-766f-4611-b5d6-652791454fca",
"created": "2014-06-30T09:15:17.182Z",
"modified": "2014-06-30T09:15:17.182Z",
"name": "x4z9arb backdoor",
"description": "This malware attempts to download remote files after establishing a foothold as a backdoor.",
"malware_types": [
"backdoor",
"remote-access-trojan"
],
"is_family": false,
"kill_chain_phases": [
{
"kill_chain_name": "mandiant-attack-lifecycle-model",
"phase_name": "establish-foothold"
}
]
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--864af2ea-46f9-4d23-b3a2-1c2adf81c265",
"created": "2020-02-29T18:03:58.029Z",
"modified": "2020-02-29T18:03:58.029Z",
"relationship_type": "indicates",
"source_ref": "indicator--d81f86b9-975b-4c0b-875e-810c5ad45a4f",
"target_ref": "malware--162d917e-766f-4611-b5d6-652791454fca"
}
]
}
№2
Adversary Bravo, — — Poison Ivy Variant d1c6.
PoisonIvy d16 , .
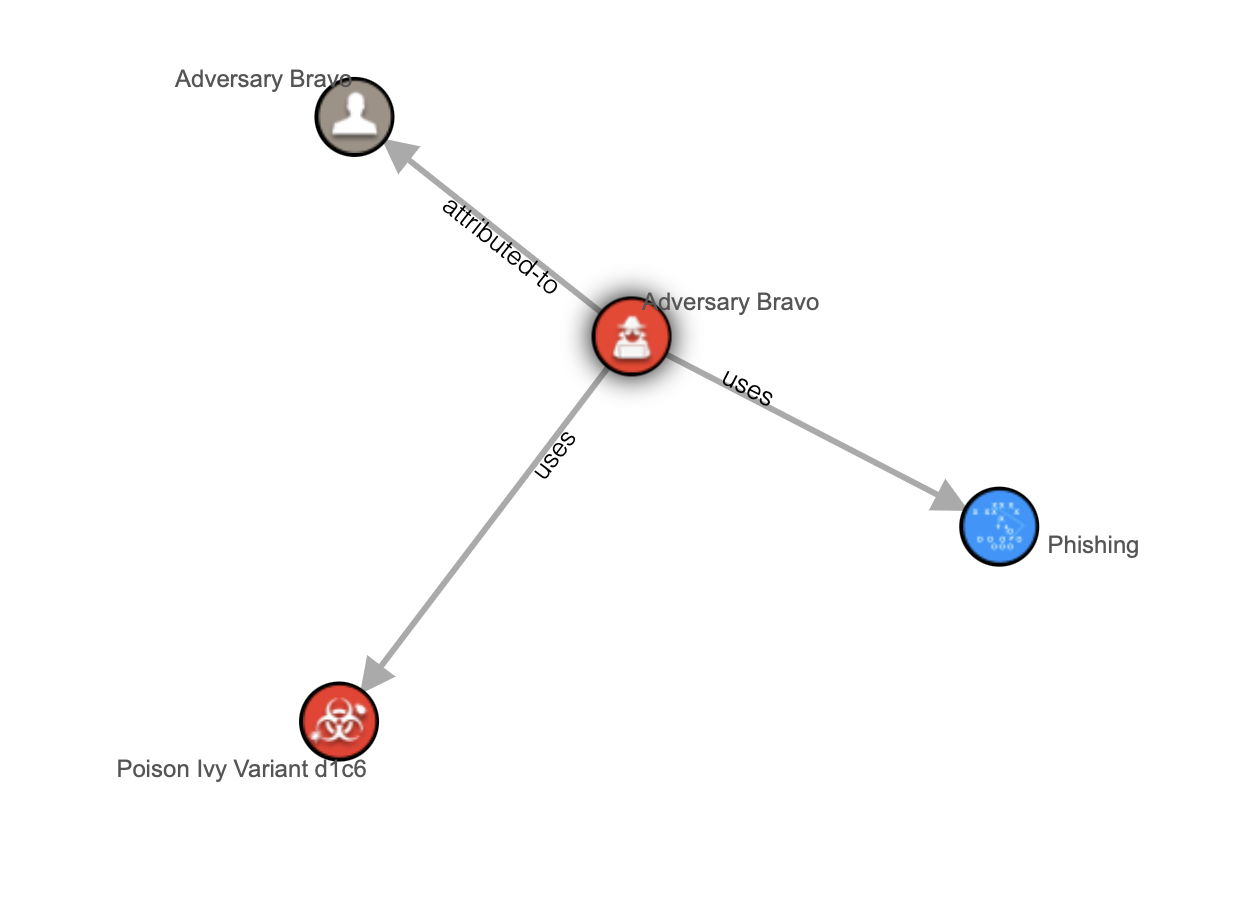
STIX 2.1
{
"type": "bundle",
"id": "bundle--0ecd8123-90d5-46e0-9cd4-65d4999b3a2e",
"objects": [
{
"type": "threat-actor",
"spec_version": "2.1",
"id": "threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
"created": "2015-05-07T14:22:14.760Z",
"modified": "2015-05-07T14:22:14.760Z",
"name": "Adversary Bravo",
"description": "Adversary Bravo is known to use phishing attacks to deliver remote access malware to the targets.",
"threat_actor_types": [
"spy",
"criminal"
]
},
{
"type": "malware",
"spec_version": "2.1",
"id": "malware--d1c612bc-146f-4b65-b7b0-9a54a14150a4",
"created": "2015-04-23T11:12:34.760Z",
"modified": "2015-04-23T11:12:34.760Z",
"name": "Poison Ivy Variant d1c6",
"malware_types": [
"remote-access-trojan"
],
"is_family": false,
"kill_chain_phases": [
{
"kill_chain_name": "mandiant-attack-lifecycle-model",
"phase_name": "initial-compromise"
}
]
},
{
"type": "attack-pattern",
"spec_version": "2.1",
"id": "attack-pattern--8ac90ff3-ecf8-4835-95b8-6aea6a623df5",
"created": "2015-05-07T14:22:14.760Z",
"modified": "2015-05-07T14:22:14.760Z",
"name": "Phishing",
"description": "Spear phishing used as a delivery mechanism for malware.",
"kill_chain_phases": [
{
"kill_chain_name": "mandiant-attack-lifecycle-model",
"phase_name": "initial-compromise"
}
],
"external_references": [
{
"source_name": "capec",
"description": "phishing",
"url": "https://capec.mitre.org/data/definitions/98.html",
"external_id": "CAPEC-98"
}
]
},
{
"type": "identity",
"spec_version": "2.1",
"id": "identity--1621d4d4-b67d-41e3-9670-f01faf20d111",
"created": "2015-05-10T16:27:17.760Z",
"modified": "2015-05-10T16:27:17.760Z",
"name": "Adversary Bravo",
"description": "Adversary Bravo is a threat actor that utilizes phishing attacks.",
"identity_class": "unknown"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--d44019b6-b8f7-4cb3-837e-7fd3c5724b87",
"created": "2020-02-29T18:18:08.661Z",
"modified": "2020-02-29T18:18:08.661Z",
"relationship_type": "uses",
"source_ref": "threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
"target_ref": "malware--d1c612bc-146f-4b65-b7b0-9a54a14150a4"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--3cd2d6f9-0ded-486b-8dca-606283a8997f",
"created": "2020-02-29T18:18:08.661Z",
"modified": "2020-02-29T18:18:08.661Z",
"relationship_type": "uses",
"source_ref": "threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
"target_ref": "attack-pattern--8ac90ff3-ecf8-4835-95b8-6aea6a623df5"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--56e5f1c8-08f3-4e24-9e8e-f87d844672ec",
"created": "2020-02-29T18:18:08.661Z",
"modified": "2020-02-29T18:18:08.661Z",
"relationship_type": "attributed-to",
"source_ref": "threat-actor--9a8a0d25-7636-429b-a99e-b2a73cd0f11f",
"target_ref": "identity--1621d4d4-b67d-41e3-9670-f01faf20d111"
}
]
}
, . . , STIX — APT1 ( json):
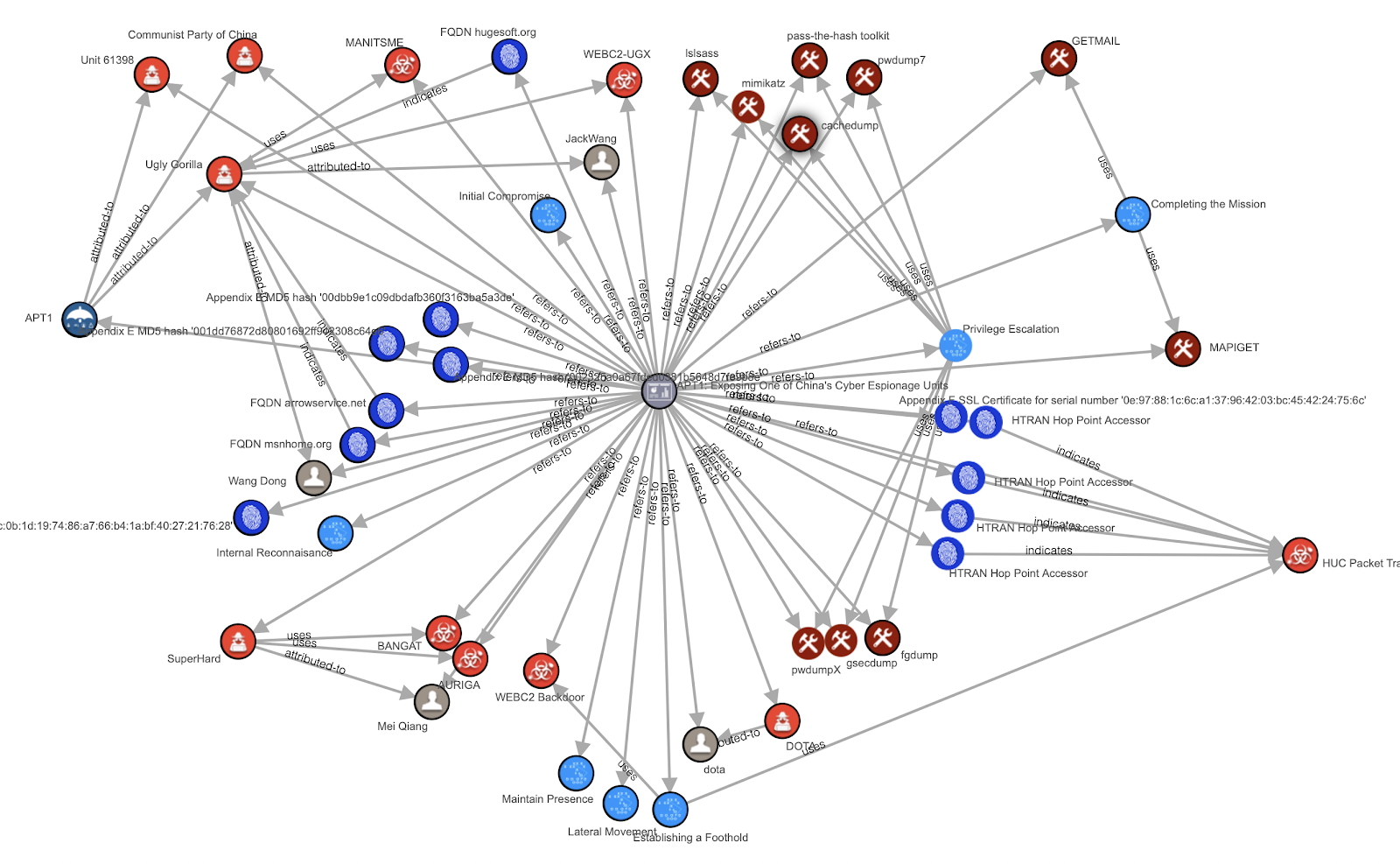
, STIX — . : , , , . — , - STIX « ».
MISP
MISP — open-source Threat Intelligence, . 2016 IETF internet draft, RFC, .
MISP p2p- threat intelligence, — . .
MISP , STIX. , MISP , :
(Event) — - , , , -. , Event — .
(Event attributes) — , . Events, , , - ( , ).
(Object) — - . , (md5, sha1. sha256) , . - Object References.
(Tag) — , , MISP Taxonomies.
(Sighting) — , , , .
(Galaxy) — , /. , . Galaxies Clusters () Elements (). : Threat Actor (Galaxy), MuddyWater (Element) — .
, adfs.senate.group adfs-senate.email, Pawn Storm, — Trend Micro.
MISP Event
"Event": {
"info": "Update on Pawn Storm: New Targets and Politically Motivated Campaigns",
"publish_timestamp": "1515851051",
"timestamp": "1515850537",
"analysis": "2",
"Attribute": [
{
"comment": "",
"category": "Network activity",
"uuid": "5a5a0b04-198c-4190-9f1a-8d1cc0a8ab16",
"timestamp": "1515850500",
"to_ids": true,
"value": "adfs.senate.group",
"object_relation": null,
"type": "hostname"
},
{
"comment": "",
"category": "Network activity",
"uuid": "5a5a0b04-4d44-463f-81a9-8d1cc0a8ab16",
"timestamp": "1515850500",
"to_ids": true,
"value": "adfs-senate.email",
"object_relation": null,
"type": "domain"
},
{
"comment": "",
"category": "External analysis",
"uuid": "5a5a0b22-86a4-4d66-90e4-9282c0a8ab16",
"timestamp": "1515850530",
"to_ids": false,
"value": "http://blog.trendmicro.com/trendlabs-security-intelligence/update-pawn-storm-new-targets-politically-motivated-campaigns/",
"object_relation": null,
"type": "link"
}
],
"Tag": [
{
"colour": "#00d622",
"exportable": true,
"name": "tlp:white"
}
],
"published": true,
"date": "2018-01-12",
"Orgc": {
"uuid": "56c42374-fdb8-4544-a218-41ffc0a8ab16",
"name": "CUDESO"
},
"threat_level_id": "3",
"uuid": "5a5a0acb-a374-415e-b88f-8d1ec0a8ab16"
}
}
MISP — , . : , , . , community-driven , , , , , STIX. , STIX — . , .
STIX MISP, threat intelligence, . , — txt csv. , STIX MISP, , , , , , . (MAEC, IODEF, CAPEC, IODEF, VERIS) — .
txt csv? — - . — ( , , ), - ( ). — plain text csv, .
plain-text — , — IP-, , , URL, — - . , , «» -, , , , .
csv , , , . , . csv, - , . , , plain-text .
, txt csv, — , . Txt , — . csv- : . , , , . — csv. , .
, , , , ( , — ), / . csv- - .
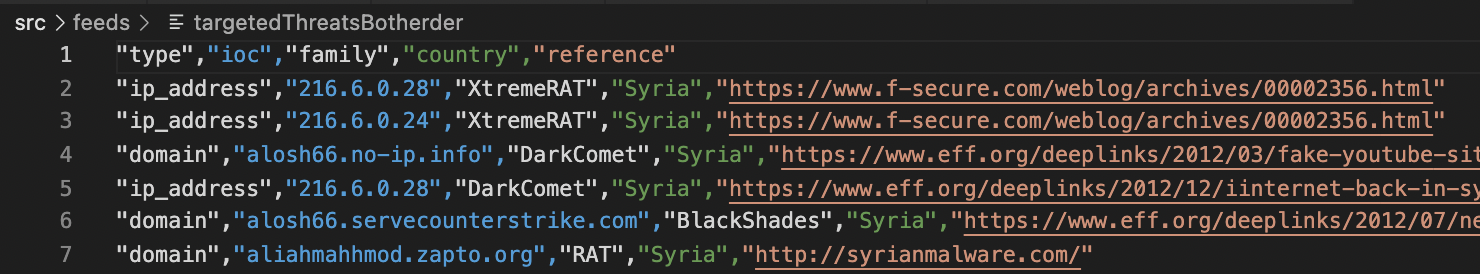
— , :

, : (URL) ()?
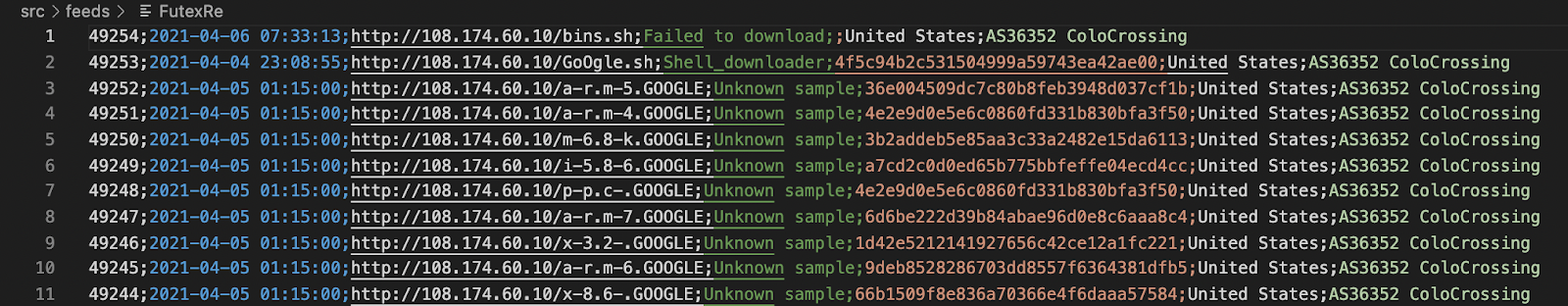
: (url, ip), — , , , . ? ? - ?
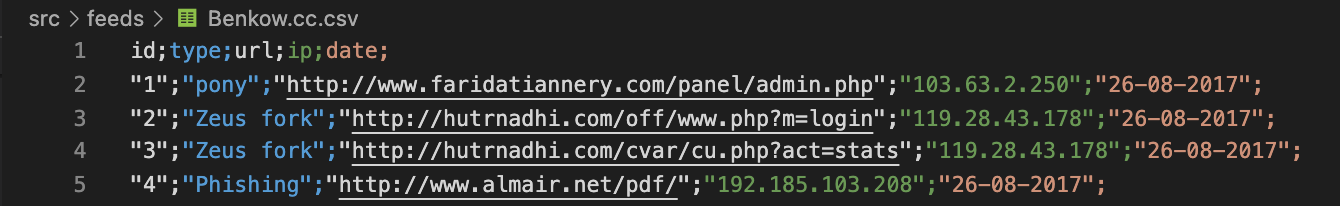
, TI, . TI, , . STIX/MISP - .
, , STIX 1.*, OpenIOC — , , , .
threat intelligence , . , , , ( ) TI. , . , txt, csv, rss, pdf.
, . , , :
https://arxiv.org/abs/2103.03530
https://res.mdpi.com/d_attachment/electronics/electronics-09-00824/article_deploy/electronics-09-00824-v3.pdf
— , . , TI. , threat intelligence — , . 100% , , . , — .
TI, — , , , — , . RST Cloud , , , . Stay tuned!