Este artículo tiene como objetivo mostrar un nuevo enfoque para la autorización en la nube, basado en un lenguaje de definición de políticas de control de acceso interpretado, llamado PERM Modeling Language (PML) . Este lenguaje se puede utilizar para expresar varios modelos de control de acceso, como Lista de control de acceso (ACL), Control de acceso basado en roles (RBAC), Control de acceso basado en atributos (ABAC) y otros. Y también hablar sobre la implementación práctica de este enfoque en la forma de una implementación específica de la biblioteca de autorización en varios idiomas de Casbin.
, , Casbin, , Microsoft Research Asia Yang Luo, , Npcap, 2019 Wireshark.
, , :
- — , , , .
- — , .
- — , , , .
:
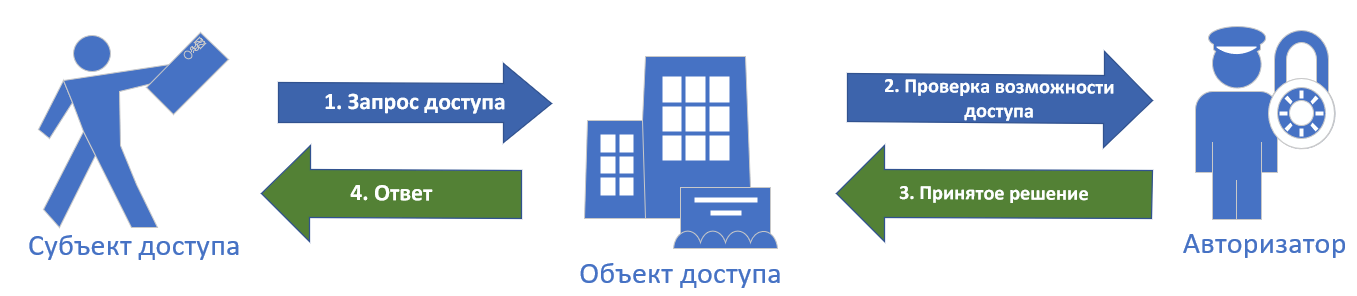
.1. .
- .
- , , .
- , . — (RBAC).
- , .
Casbin
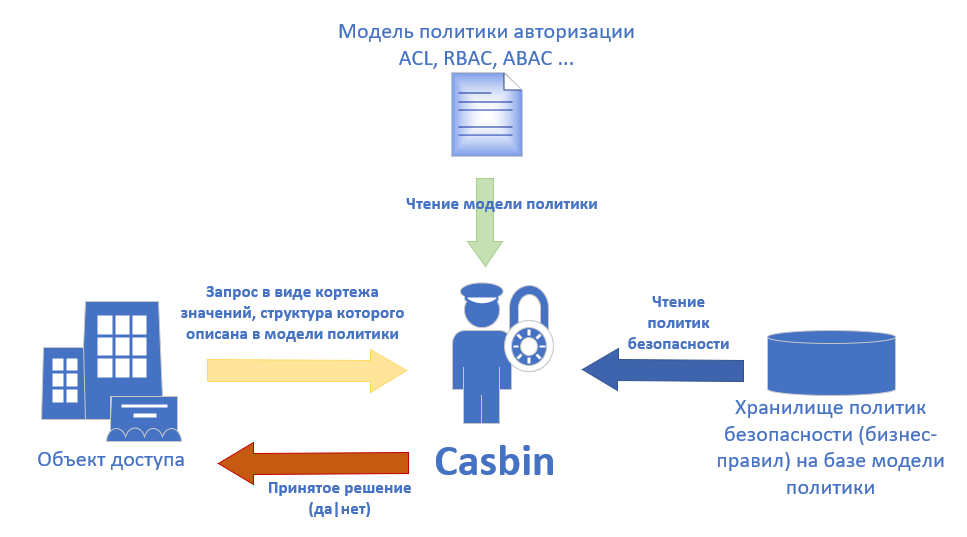
Casbin — , , ACL, RBAC, ABAC .. .1 — Casbin .

.2. Casbin.
Casbin . *.CONF PERM (Policy, Effect, Request, Matchers), .
, , , . *.csv
, , , .
, PERM — . (Policy — , Effect — , Request — , Matchers — ). PERM .CONF, , 4 , .
№1. (ACL)
PERM .
, CRM , , ,
(client). (Access Control List — ACL).
, , , client
:
| / | (client.create) | (client.read) | (client.modify) | (client.delete) |
|---|---|---|---|---|
| (alice) | ||||
| (bob) | ||||
| (peter) |
client_acl_model.conf
PERM,
[request_definition] r = sub, obj, act [policy_definition] p = sub, obj, act [policy_effect] e = some(where (p.eft == allow)) [matchers] m = r.sub == p.sub && r.obj == p.obj && r.act == p.act
=
. .
[request_definition]
(r
). , , sub
(), obj
(), act
(). , , : ["alice","client","read"]
( alice
read
client
?).
[policy_definition]
. , . , eft
, allow
() deny
(). , ACL , .
[policy_effect]
, , , . CRM e = some(where (p.eft == allow))
, : - allow
(,eft
== "allow"), allow
(). , deny
(), deny
.
[matchers]
, (r
) (p
).
, r.sub
p.sub
(&&
) r.obj == p.obj
, r.act == p.act
.
. — [policy_definition] . , , * .csv
client_acl_policy.csv
:
p, alice, client, create p, alice, client, read p, alice, client, modify p, alice, client, delete p, bob, client, read p, peter, client, create p, peter, client, read p, peter, client, modify
, , , eft , allow
(). -, - deny
.
.
— , Casbin CRM .
, C#, , , , .
.net Casbin Enforcer
, , , , .
// Enforcer var e = new Enforcer("path/to/client_acl_model.conf", "path/to/client_acl_policy.csv"); // , var sub = "alice"; var obj = "client"; var act = "read"; // if (e.Enforce(sub, obj, act)) { // alice client } else { // , }
№2. (RBAC)
, , , . , , .
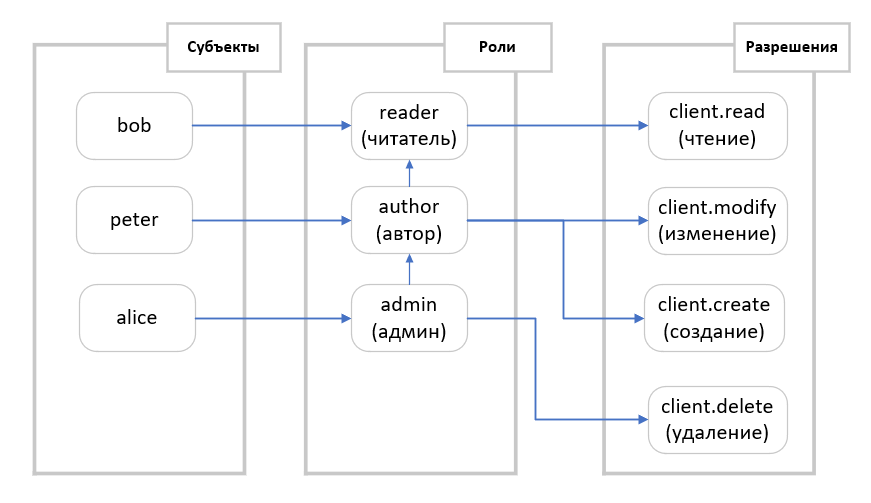
.3. (RBAC).
. bob
(reader
), peter
(author
), alice
CRM (admin
).
( , , ?, ACL, ?). , . , , .
, client_rbac_model.conf
:
[request_definition] r = sub, obj, act [policy_definition] p = sub, obj, act [role_definition] g = _, _ [policy_effect] e = some(where (p.eft == allow)) [matchers] m = g(r.sub, p.sub) && r.obj == p.obj && r.act == p.act
, [role_definition]
. g = _, _
, [matchers]
— r.sub
p.sub
, , , . .
, ACL — [matchers]
r.sub == p.sub
g (r.sub, p.sub)
, : r.sub
( ) p.sub
.
client_rbac_policy.csv
:
p, reader, client, read p, author, client, modify p, author, client, create p, admin, client, delete g, bob, reader g, peter, author g, alice, admin g, author, reader g, admin, author
c ACL, :
var e = new Enforcer("path/to/client_rbac_model.conf", "path/to/client_rbac_policy.csv"); var sub = "alice"; var obj = "client"; var act = "read"; // if (e.Enforce(sub, obj, act)) { // alice client } else { // , }
№3. (RBAC with domains/tenants)
CRM, , — , , , , . Bob , CRM.
, , client_rbac_with_domain_model.conf
. , , .
[request_definition] r = sub, dom, obj, act [policy_definition] p = sub, dom, obj, act [role_definition] g = _, _, _ [policy_effect] e = some(where (p.eft == allow)) [matchers] m = g(r.sub, p.sub, r.dom) && r.dom == p.dom && r.obj == p.obj && r.act == p.act
№2 (RBAC) [request_definition]
[policy_definition]
dom
, , , .
[role_definition]
, , , g = _, _
g = _, _, _
.
[matchers]
g(r.sub, p.sub)
g(r.sub, p.sub, r.dom) && r.dom == p.dom
, : r.sub
( ) p.sub
c r.dom
, r.dom
, p.dom
.
client_rbac_with_domain_policy.csv
:
p, reader, company1, client, read p, author, company1, client, modify p, author, company1, client, create p, admin, company1, client, delete p, reader, company2, client, read p, author, company2, client, modify p, author, company2, client, create p, admin, company2, client, delete g, author, reader, company1 g, admin, author, company1 g, author, reader, company2 g, admin, author, company2 g, alice, admin, company1 g, peter, author, company1 g, bob, admin, company2
№4. RESTFul
, RestAPI URI /res/*,/res/:id, HTTP GET,POST,PUT,DELETE.
[matchers].
( Casbin):
[request_definition] r = sub, obj, act [policy_definition] p = sub, obj, act [policy_effect] e = some(where (p.eft == allow)) [matchers] m = r.sub == p.sub && keyMatch(r.obj, p.obj) && regexMatch(r.act, p.act)
:
p, alice, /alice_data/*, GET p, alice, /alice_data/resource1, POST p, bob, /alice_data/resource2, GET p, bob, /bob_data/*, POST p, cathy, /cathy_data, (GET)|(POST)
№5. (ABAC)
, ABAC , , , , , ( ABAC). ABAC XACML. , ABAC Casbin : , .
, , Casbin.
ABAC:
[request_definition] r = sub, obj, act [policy_definition] p = sub, obj, act [policy_effect] e = some(where (p.eft == allow)) [matchers] m = r.sub == r.obj.Owner
, , [matchers], r.sub
Owner
, r.obj
, e.Enforce()
. , Casbin Reflection, Owner
.
, r.obj
, :
public class ResourceObject { ... public string Owner { get; set; } }
ABAC ,
[matchers] m = r.sub.Domain == r.obj.Domain
, ABAC (r
), r.sub
, r.obj
, r.act
..
ABAC (p
), p.sub
, p.obj
.., Casbin.
ABAC, ABAC Casbin, [matchers]
.
eval()
— .
abac_scale_model.conf
[request_definition] r = sub, obj, act [policy_definition] p = sub_rule, obj, act [policy_effect] e = some(where (p.eft == allow)) [matchers] m = eval(p.sub_rule) && r.obj == p.obj && r.act == p.act
[policy_definition]
, sub_rule
, [matchers]
eval(p.sub_rule)
. p.sub_rule
( ), , .
abac_scale_policy.conf
:
p, r.sub.Age > 18, client1, read p, r.sub.Age < 60, client2, write
:
public class User { public int Age { get; set;} public string Name { get; set; } } class Program { static void Main(string[] args) { var e = new Enforcer("path/to/abac_scale_model.conf", "path/to/abac_scale_policy.csv"); var sub = new User() { Name = "alice", Age = 19 }; var obj = "client1"; var act = "read"; if (e.Enforce(sub, obj, act)) { // alice client1 } else { // , } } }
Casbin — , PERM (PML). , , , .
Casbin (policy model) PERM, , (policy) .
.